Introduction
As Australia steps up its digital transformation, app security is now a primary concern for startups, corporates, and government-backed platforms alike. With advanced cyber threats and strict national regulations, building a secure app in 2025 means much more than encrypting logins—it requires a holistic, compliance-driven approach that covers every stage of the software lifecycle. This guide covers everything you need to know, from regulations and technical controls to security-first DevOps and ongoing maintenance.
Key Australian Security Regulations and Frameworks

-
Privacy Act 1988 & APPs: The foundation of data privacy in Australia. Your app must comply with 13 Australian Privacy Principles, covering data collection, storage, consent, access, and correction.
-
Cyber Security Bill 2024: Part of Australia’s national strategy—mandates regular security testing and proactive strategies across all digital services.
-
Consumer Data Right (CDR): Grants users power over their data and enforces encrypted, permission-based sharing (especially for fintech, energy, health, and telecom apps).
-
ACSC Essential Eight: Critical mitigation strategies from the Australian Cyber Security Centre, such as application whitelisting, multi-factor authentication (MFA), and prompt patching.
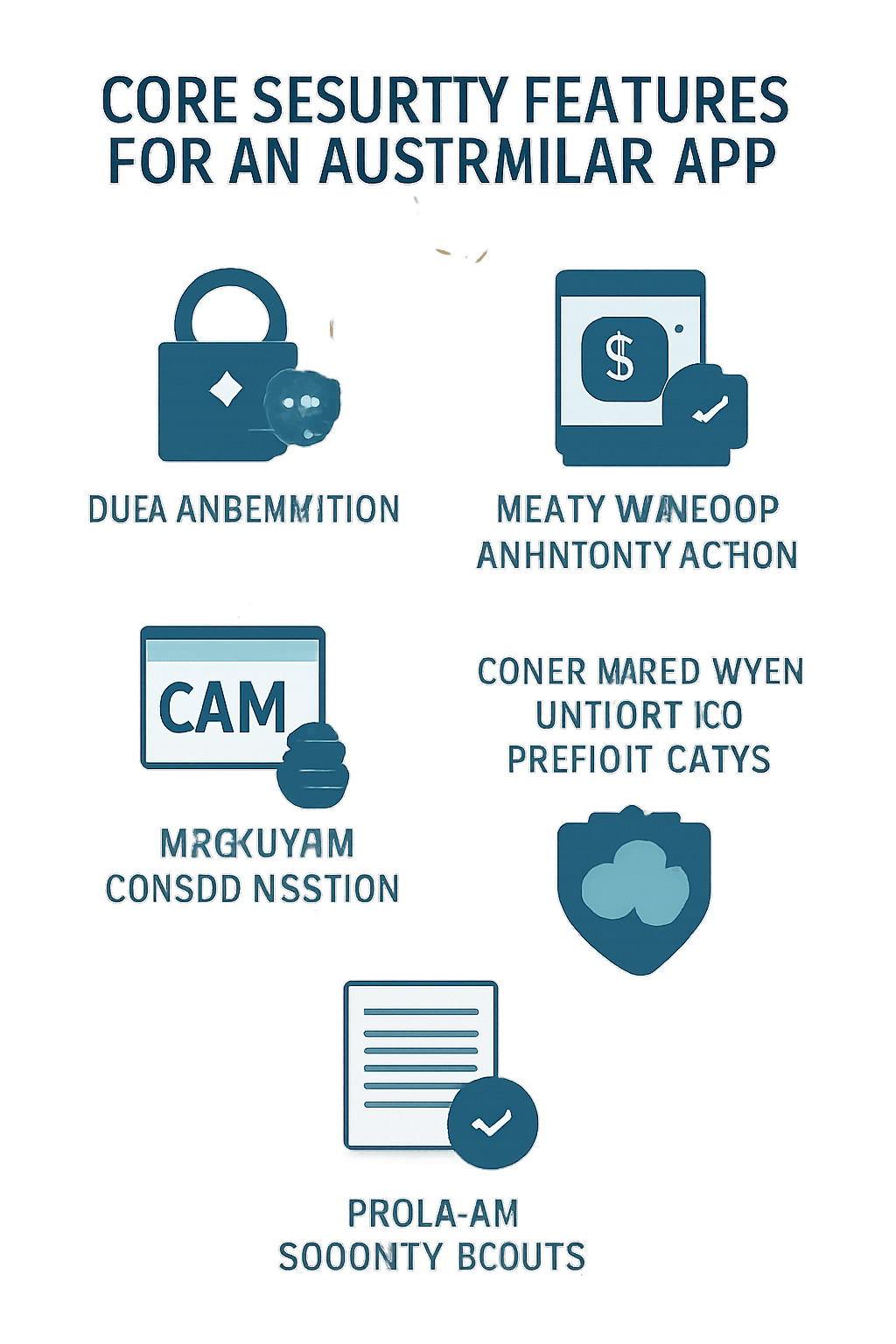
Core Features for Securing an Australian App
-
End-to-End Encryption:
Encrypt all data in transit (user–server, API, third party) and at rest (device, cloud) using robust algorithms. -
Multi-Factor Authentication (MFA):
Integrate frameworks for MFA, with support for biometrics and one-time passwords. -
Role-Based Access Control (RBAC):
Restrict user and admin permissions based on roles, minimizing access to sensitive data. -
Secure APIs:
Use HTTPS, OAuth 2.0, JWT tokens, and strict input validation to prevent API exploits. -
Comprehensive Logging and Monitoring:
Track user actions and anomalies for rapid detection, audits, and incident response. -
Patching and Upgrades:
Keep dependencies current and patch vulnerabilities quickly, including those in third-party code. -
Compliance Dashboards:
Centralize reporting for legal audits and provide automated alerts for non-compliance.
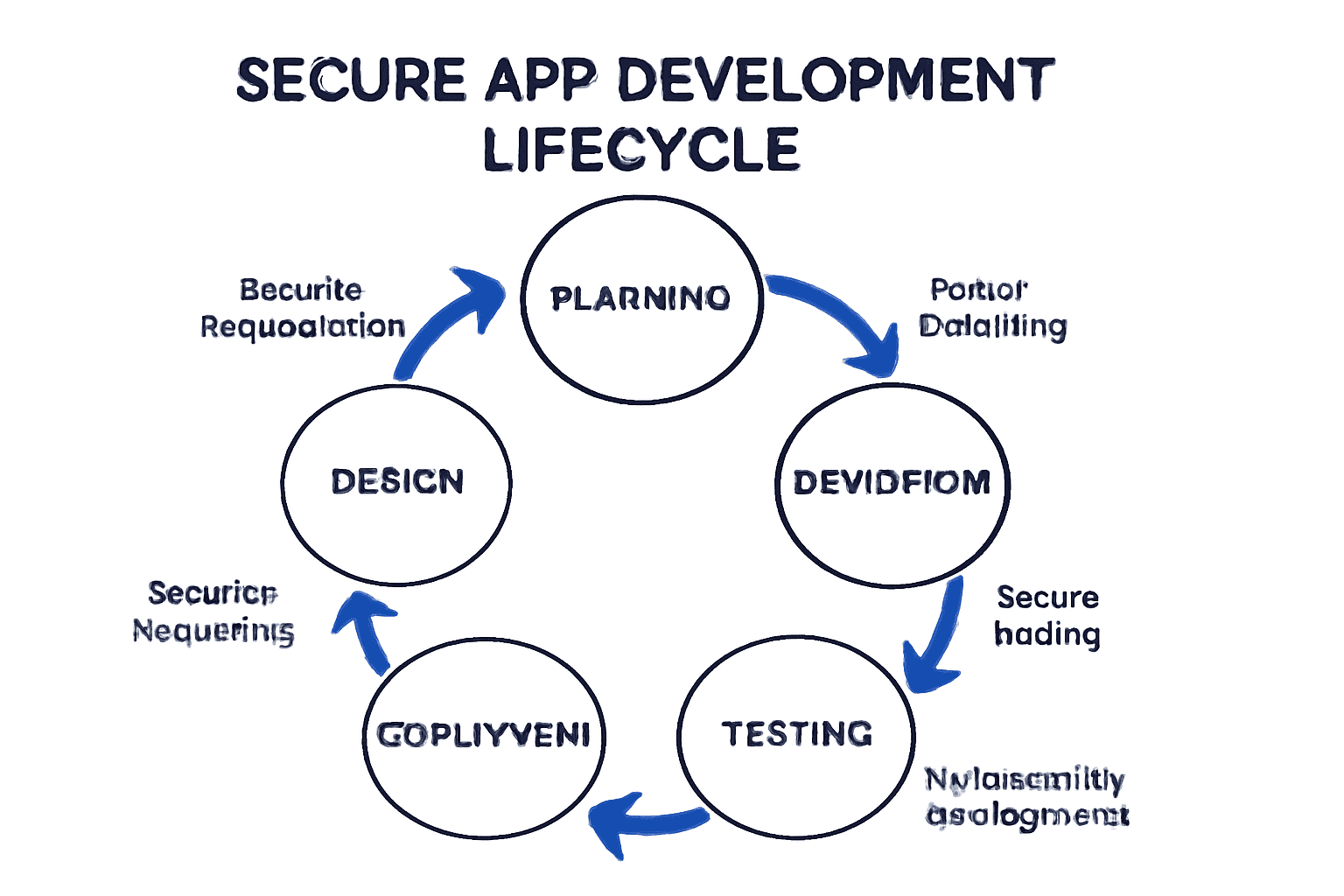
Secure App Development Lifecycle
-
Planning: Embed security and compliance goals from day one. Map data flows, model threats, and document all regulatory requirements.
-
Development: Enforce secure coding practices, code reviews, static and dynamic code analysis, and minimize hardcoded secrets.
-
Testing: Use SAST, DAST, and regular penetration testing. Validate your app against all current regulatory checklists.
-
Deployment: Harden infrastructure, enforce API keys/credentials management, enable HTTPS everywhere, and use infrastructure-as-code for secure, repeatable builds.
-
Ongoing Maintenance: Monitor for threats 24/7, apply critical security patches, and train your development team on the latest exploits and mitigations. Include real incident and breach response plans in policy documents.
2025 Security Trends for Australian Apps

-
AI and ML Threat Intelligence: Use AI-powered monitoring for real-time anomaly detection and automated response.
-
Cloud Security Posture Management (CSPM): Automated review of your cloud setup for misconfigurations or vulnerabilities.
-
DevSecOps: Integrate security into your CI/CD pipeline to catch vulnerabilities before release.
-
Post-Quantum Cryptography: Begin evaluating quantum-resistant encryption, especially for finance and government apps.
-
Software Supply Chain Security: Monitor and document all third-party libraries/SBOMs to patch supply-chain threats rapidly.
Overcoming Common Challenges

-
Evolving Threats: Proactively adopt AI-based security solutions and maintain strong ties with cybersecurity experts and Australian government resources.
-
User Experience vs. Security: Use frictionless MFA (biometrics), smart session management, and clear notifications to balance security with user delight.
-
Multi-Jurisdictional Compliance: Architect your app for modular compliance, making it easy to adjust for international rules (like GDPR or CCPA) when expanding.
Conclusion
Building a secure app in Australia in 2025 means thoroughly integrating regulatory compliance, technical controls, and proactive threat intelligence into your development process. Start with security at the planning stage, close every gap with modern frameworks and ongoing audits, and always act on the principle that securing your users’ data is the cornerstone of building trust, credibility, and long-term business success.
For expert support, compliance consulting, and secure digital product development, consider partnering with industry leaders such as TechOTD.
FAQ
1. What are must-haves for secure app development in Australia?
End-to-end encryption, role-based access, secure coding, regular audits, compliance with the Privacy Act, and ongoing threat monitoring.
2. Which regulations are most important for my app?
The Privacy Act 1988, Cyber Security Bill 2024, Consumer Data Right, and ACSC’s Essential Eight are crucial for all major industries.
3. Is compliance optional?
Absolutely not—non-compliance risks fines, lawsuits, reputation loss, and app bans.
4. How do I keep up with threats?
Adopt DevSecOps, use AI-based monitoring, engage in regular training, and partner with security experts.
5. Can my team do this alone?
Many choose to work with specialist partners for compliance
and complex technical challenges. Review TechOTD’s web and AI offerings for expert help.