Introduction
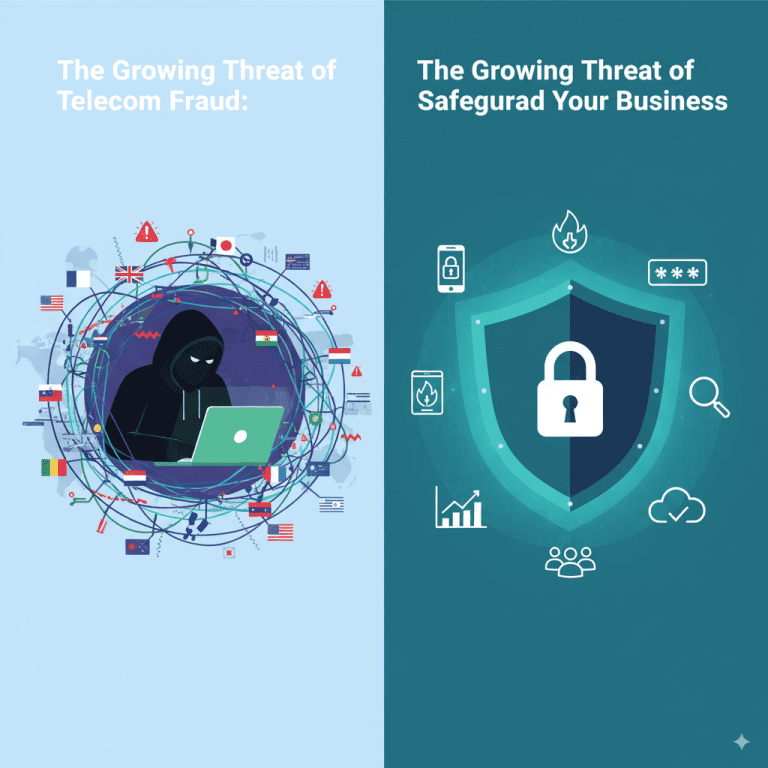
As telecom networks become increasingly vital to global communications and business operations, the threat of telecom fraud has escalated into a pressing concern. Fraudsters exploit vulnerabilities within telecom infrastructures to commit crimes ranging from unauthorized access and identity theft to call and subscription fraud. For businesses relying heavily on telecom services, these fraudulent activities can result in significant financial losses, reputational damage, and regulatory penalties.
This blog explores the evolving nature of telecom fraud, common fraud schemes targeting businesses, and robust strategies to safeguard your telecom assets. Leveraging AI-driven security solutions and advanced analytics is becoming indispensable to stay ahead of increasingly sophisticated attacks. For businesses seeking intelligent risk assessment and security planning, TechOTD’s AI services offer transformative solutions tailored to telecom and other industries.
Understanding Telecom Fraud: Types and Tactics
Telecom fraud continues to evolve with the advent of new technologies like VoIP, 5G, and mobile networks. Common types include:
-
Subscription Fraud: Fraudsters obtain services under false identities, leaving businesses with unpaid bills.
-
Call Forwarding Fraud: Unauthorized redirection of calls to premium rate numbers to exploit call charges.
-
PBX Hacking: Unauthorized access to private branch exchanges, generating fraudulent calls.
-
Refiling and Phishing: Illegitimate use of telecom resources to conduct phishing or refile previous calls to mask origins.
-
SIM Swap Fraud: Hijacking mobile numbers to bypass authentication controls.
-
International Revenue Share Fraud (IRSF): Exploiting international call setups to generate revenue for fraudsters at the operators’ expense.
Each scheme targets vulnerabilities in telecom infrastructure, emphasizing the need for proactive defense mechanisms.
Business Impacts of Telecom Fraud
-
Financial Losses: Millions lost annually through fraudulent call charges, service theft, and identity compromise.
-
Operational Disruption: Network overloads and compromised services degrade customer experience.
-
Regulatory and Compliance Risks: Failure to protect telecom assets can lead to penalties under data protection laws and industry regulations.
-
Brand Reputation Damage: Customer trust erodes when fraud incidents are publicized.
How to Safeguard Your Business Against Telecom Fraud
1. Implement AI-Powered Fraud Detection and Analytics
AI systems monitor traffic patterns in real time to detect anomalies that indicate potential fraud. Machine learning models adapt to new fraud behaviors, minimizing false positives and enabling quick action.
Learn about predictive analytics enhancing telecom security here:
Predictive Analytics Features and Use Cases.
2. Strengthen Identity and Access Management
Multi-factor authentication (MFA) for network access, strict user identity verification, and SIM swap detection mechanisms decrease unauthorized entry risk.
3. Secure Network Architecture and Protocols
Deploy firewalls, encryption, and secure routing protocols. Regularly update PBX and VoIP systems to patch vulnerabilities.
4. Continuous Monitoring and Incident Response
Establish 24/7 network surveillance, combining automated alerts and expert reviews. Develop a clear fraud response plan and staff training.
5. Collaborate with Telecom Partners
Work closely with carriers and technology providers to share threat intelligence and integrate security operations.
Explore how blockchain enhances telecom security and trust:
Blockchain Integration in Dubai Business Processes.
Leveraging TechOTD’s Expertise in Telecom Security
TechOTD provides tailored AI and machine learning solutions focused on telecom fraud detection, risk assessment, and workflow automation. Their expert consulting services help businesses evaluate vulnerabilities, implement advanced fraud controls, and comply with industry standards.
Discover their approach to securing telecom through intelligent automation:
How TechOTD Works.
Future Trends in Combating Telecom Fraud
-
AI and Deep Learning: Enhanced detection capabilities with evolving fraud patterns.
-
Cloud-Based Security: Scalable, centralized fraud monitoring platforms.
-
5G Security Innovations: Addressing unique vulnerabilities in emerging networks.
-
Integration of Big Data Analytics: Deeper insights into complex fraud schemes.
The synergy of AI with telecom infrastructure will be key to staying ahead in this security arms race.
Conclusion
Telecom fraud is a pervasive and growing threat to business continuity and profitability. Safeguarding telecom assets requires a blend of cutting-edge AI technologies, robust protocols, and collaborative efforts across the ecosystem. Businesses investing in these defenses, with expert partners like TechOTD, can not only mitigate losses but also build trust and resilience in an increasingly connected world.
For comprehensive AI-powered security solutions and insights, visit TechOTD AI Services and explore their extensive technology blog.
FAQs
Q1: What is the most common telecom fraud for businesses?
Subscription fraud and PBX hacking are among the most prevalent and costly.
Q2: How does AI help prevent telecom fraud?
AI detects unusual traffic patterns and adapts to new fraud techniques in real time.
Q3: Can blockchain improve telecom security?
Yes, blockchain provides immutable and transparent transaction records that reduce fraud risks.
Q4: What role does continuous monitoring play?
It enables early fraud detection and rapid incident response, minimizing damage.
Q5: Why is collaboration important in telecom fraud prevention?
Sharing threat intelligence and best practices enhances the overall ecosystem security.